Penetration Testing
A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration testing is commonly used to augment a web application firewall (WAF).
Pen testing can involve the attempted breaching of any number of application systems, (e.g., application protocol interfaces (APIs), frontend/backend servers) to uncover vulnerabilities, such as unsanitized inputs that are susceptible to code injection attacks.
Insights provided by the penetration test can be used to fine-tune your WAF security policies and patch detected vulnerabilities.
Penetration testing stages
The pen testing process can be broken down into five stages.
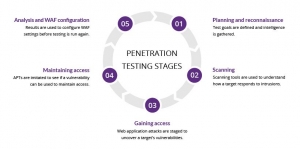
1. Planning and reconnaissance
The first stage involves:
- Defining the scope and goals of a test, including the systems to be addressed and the testing methods to be used.
- Gathering intelligence (e.g., network and domain names, mail server) to better understand how a target works and its potential vulnerabilities.
2. Scanning
The next step is to understand how the target application will respond to various intrusion attempts. This is typically done using:
- Static analysis – Inspecting an application’s code to estimate the way it behaves while running. These tools can scan the entirety of the code in a single pass.
- Dynamic analysis – Inspecting an application’s code in a running state. This is a more practical way of scanning, as it provides a real-time view into an application’s performance.
3. Gaining Access
This stage uses web application attacks, such as cross-site scripting, SQL injection and backdoors, to uncover a target’s vulnerabilities. Testers then try and exploit these vulnerabilities, typically by escalating privileges, stealing data, intercepting traffic, etc., to understand the damage they can cause.
4. Maintaining access
The goal of this stage is to see if the vulnerability can be used to achieve a persistent presence in the exploited system— long enough for a bad actor to gain in-depth access. The idea is to imitate advanced persistent threats, which often remain in a system for months in order to steal an organization’s most sensitive data.
5. Analysis
The results of the penetration test are then compiled into a report detailing:
- Specific vulnerabilities that were exploited
- Sensitive data that was accessed
- The amount of time the pen tester was able to remain in the system undetected
Penetration testing methods
External testing
External penetration tests target the assets of a company that are visible on the internet, e.g., the web application itself, the company website, and email and domain name servers (DNS). The goal is to gain access and extract valuable data.
Internal testing
In an internal test, a tester with access to an application behind its firewall simulates an attack by a malicious insider. This isn’t necessarily simulating a rogue employee. A common starting scenario can be an employee whose credentials were stolen due to a phishing attack.
Blind testing
In a blind test, a tester is only given the name of the enterprise that’s being targeted. This gives security personnel a real-time look into how an actual application assault would take place.
Double-blind testing
In a double blind test, security personnel have no prior knowledge of the simulated attack. As in the real world, they won’t have any time to shore up their defenses before an attempted breach.
Targeted testing
In this scenario, both the tester and security personnel work together and keep each other appraised of their movements. This is a valuable training exercise that provides a security team with real-time feedback from a hacker’s point of view.
penetration test tools:

Replicate Attacks
Identify Vulnerabilities
Validate Remediation
Flexible Pricing for Every Use Case

Acunetix is a fully automated penetration testing tool. Its web application security scanner accurately scans HTML5, JavaScript and Single-page applications. It can audit complex, authenticated webapps and issues compliance and management reports on a wide range of web and network vulnerabilities, including out-of-band vulnerabilities.
Features:
- Scans for all variants of SQL Injection, XSS, and 4500+ additional vulnerabilities
- Detects over 1200 WordPress core, theme, and plugin vulnerabilities
- Fast & Scalable – crawls hundreds of thousands of pages without interruptions
- Integrates with popular WAFs and Issue Trackers to aid in the SDLC
- Available On Premises and as a Cloud solution.

This is the most popular and advanced Framework that can be used for pentest. It is an open source tool based on the concept of ‘exploit’ which means you pass a code that breach the security measures and enter a certain system. If entered, it runs a ‘payload’, a code that performs operations on a target machine, thus creating the perfect framework for penetration testing. It is a great testing tool test whether the IDS is successful in preventing the attacks that we bypass it
Metaspoilt can be used on networks, applications, servers, etc. It has a command line and GUI clickable interface, works on Apple Mac OS X, works on Linux and Microsoft Windows.
Features of Metaspoilt
- Basic command line interface
- Third party import
- Manual brute forcing
- Manual brute forcing
- website penetration testing

Nessus has been used as a security penetration testing tool for twenty years. 27,000 companies utilize the application worldwide. The software is one of the most powerful testing tools on the market with over 45,000 CEs and 100,000 plugins. Ideally suited for scanning IP addresses, websites and completing sensitive data searches. You will be able to use this to locate ‘weak spots’ in your systems.
The tool is straightforward to use and offers accurate scanning, and at the click of a button, providing an overview of your network’s vulnerabilities. The pen test application scans for open ports, weak passwords, and misconfiguration errors.
Benefits:
- Ideal for locating and identify missing patches as well as malware.
- The system only has .32 defects per every 1 million scans.
- You can create customized reports including types of vulnerabilities by plugin or host.
- In addition to web application, mobile scanning, and cloud environment, the tool offers priority remediation.
Penetration Test standards

The Open Web Application Security Project (OWASP) is a worldwide non-profit organization focused on improving the security of software. The project has multiple tools to pen test various software environments and protocols. Flagship tools of the project include
- Zed Attack Proxy (ZAP – an integrated penetration testing tool)
- OWASP Dependency Check (it scans for project dependencies and checks against know vulnerabilities)
- OWASP Web Testing Environment Project (collection of security tools and documentation)
The OWASP testing guide gives “best practice” to penetration test the most common web application

OSSTMM is a methodology to test the operational security of physical locations, workflow, human security testing, physical security testing, wireless security testing, telecommunication security testing, data networks security testing and compliance. OSSTMM can be supporting reference of IOS 27001 instead of a hands-on penetration testing guide.
OSSTMM includes the following key sections:
Operational Security Metrics , Trust Analysis , Work Flow , Human Security Testing , Physical Security Testing , Wireless Security Testing , Telecommunications Security Testing , Data Networks Security Testing , Compliance Regulations , Reporting with the STAR (Security Test Audit Report).
TaktaCom Group is one of the few companies that offering penetration test services , Provides all phases of work as documented.
Contact us for more information
